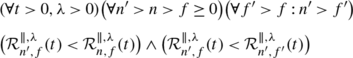- Erratum
- Open access
- Published:
Erratum to: On the reliability and availability of replicated and rejuvenating systems under stealth attacks and intrusions
Journal of the Brazilian Computer Society volume 18, page 267 (2012)
Erratum to: J Braz Comput Soc (2012) 18:61–80
The following is a list of corrections to several typos found in the original online version of [1]:
-
in the caption of Fig. 10 (p. 75, right column) the correct analytic expression used to draw the reference curve (e,
 ) was (1−e−r)/r, rather than (1−er)/r;
) was (1−e−r)/r, rather than (1−er)/r; -
Equation (10) (p. 79, left column) should be
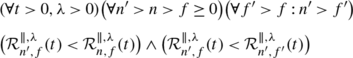
-
Equation (14) (p. 79, left column) is valid for t>0.
References
Brandão LTAN, Bessani AN (2012) On the reliability and availability of replicated and rejuvenating systems under stealth attacks and intrusions. J Braz Comput Soc 18:61–80. doi:10.1007/s13173-012-0062-x
Author information
Authors and Affiliations
Corresponding author
Additional information
The online version of the original article can be found under doi:10.1007/s13173-012-0062-x.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License ( https://creativecommons.org/licenses/by/2.0 ), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Teixeira d’Aguiar Norton Brandão, L., Neves Bessani, A. Erratum to: On the reliability and availability of replicated and rejuvenating systems under stealth attacks and intrusions. J Braz Comput Soc 18, 267 (2012). https://doi.org/10.1007/s13173-012-0074-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13173-012-0074-6
 ) was (1−e−r)/r, rather than (1−er)/r;
) was (1−e−r)/r, rather than (1−er)/r;